- Overview and analysis of the current information available on Oracle cloud breach that might be affecting Moroccan orgs.
- The breach is not yet confirmed, but strong indications suggest otherwise.
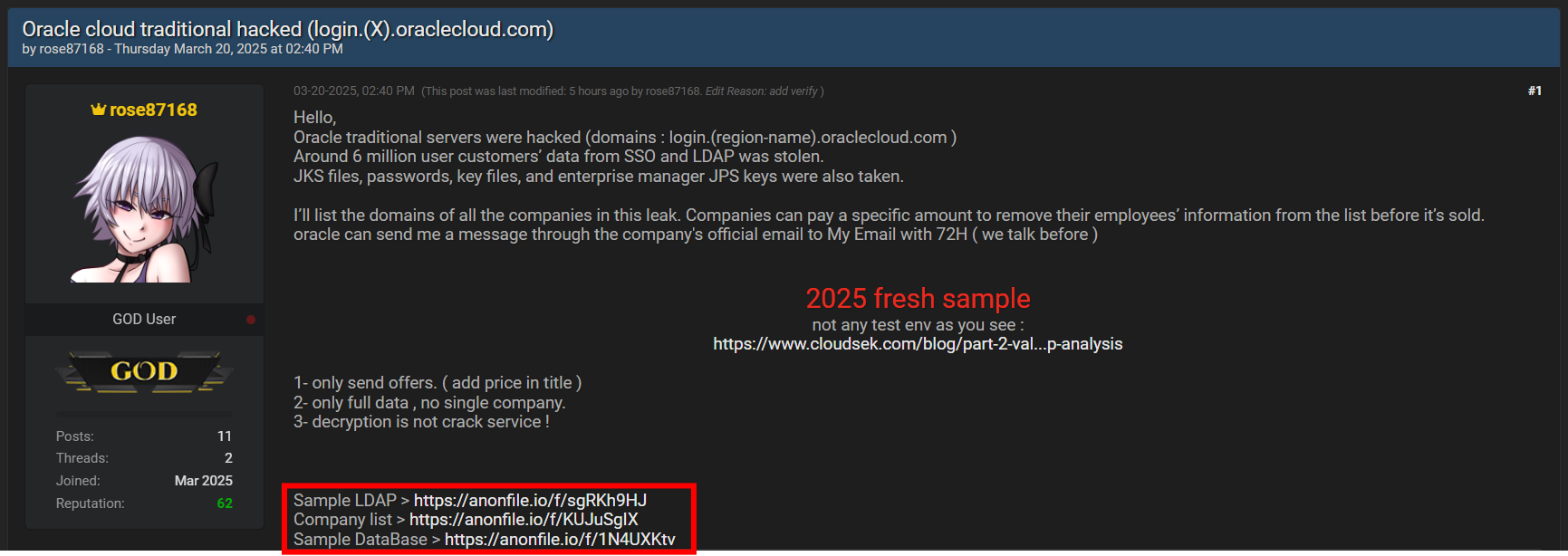
On the 20th of March a threat actor under the name of rose87168 claimed that he breached Oracle cloud and exfiltrated ~6 Million records from SSO and LDAP, The actor claims stealing JKS files, passwords, key files, and enterprise manager JPS keys.

Even though Oracle denied the breach the threat actor on X/Twitter proved breaching login.us2.oraclecloud.com (Archived on Wayback machine) that was later taken down by oracle, historically the subdomain was hosting oracle fusion middleware server , which was impacted with critical CVE-2021-35587 affecting Oracle Access Manager, then added later to CISA KEV (CVE-2021-35587 Known Exploited Vulnerabilities) on December 2022.
oracle denied breach :)) https://t.co/f4r4HmISb7
— rose87168 (@rose87168) March 24, 2025
can anyone explain how i do this ?
The impact varies though based on what the actor claims he leaked (JKS, SSO passwords and others), this is the severity of the leaked components :
| Component | Function | Impact | Severity |
|---|---|---|---|
| JKS Files (Java KeyStore) | Private keys, SSL/TLS certificates, authentication credentials | - Compromised SSL/TLS encryption, leading to Man-in-the-Middle (MITM) attacks. - Unauthorized access to secured Java applications. - Risk of digital signature forgery. |
🔴 High |
| Encrypted SSO Passwords | User authentication credentials for Single Sign-On (SSO) | - Attackers can decrypt passwords and gain unauthorized access. - Users’ accounts and sensitive data at risk. - Potential privilege escalation and identity theft. |
🔴 Critical |
| Key Files | Private keys for encryption, authentication (SSL, SSH, etc.) | - Loss of data confidentiality (if attackers decrypt files). - Unauthorized remote access via leaked SSH keys. - Compromise of secure communication (SSL/TLS keys). |
🔴 High |
| Enterprise Manager JPS Keys | Oracle WebLogic/Fusion Middleware security keys & credentials | - Attackers can decrypt WebLogic credentials, leading to full admin access. - Risk of data exfiltration and service disruptions. - Compromise of enterprise applications and sensitive database credentials. |
🔴 Critical |
The impact on Moroccan companies :
- The attacker has also shared a file claiming to include the impacted entities around the world :
- We filtered the file and extracted all the potential affected Moroccan companies/orgs based on the TLD (.ma) which yielded potentially 83 affected with this breach, note if your organisation included in the list it doesn't mean you we're directly targeted but your 3rd party provider (Oracle in this case) was breached.
The listed Moroccan companies extracted from company_list.txt shared by the actor :
- cihbank.ma
- cdg.ma
- cih.co.ma
- omnidata.ma
- state.ma
- hps.ma
- mem.gov.ma
- sirecom.ma
- mtsgroup.ma
- segep.ma
- jud.state.ma
- dot.state.ma
- omniacademy.ma
- microdata.ma
- emi.ac.ma
- bms-emea.ma
- corporate.ma
- par3.ma
- parevent.ma
- ban.ma
- gbe.ma
- emaa.ma
- mediexperts.ma
- istyle.ma
- um6p.ma
- etu.uae.ac.ma
- um5r.ac.ma
- usmba.ac.ma
- ddm.ma
- axelink.ma
- student.1337.ma
- compucom.ma
- dataprotect.ma
- datalink.ma
- prometi.ma
- dprgroup.ma
- orsys.co.ma
- uir.ac.ma
- ago-solutions.ma
- tcs.ma
- enova.ma
- nplusone.ma
- onecloud.ma
- s2m.net.ma
- jway.ma
- i-team.ma
- ecintelligence.ma
- innovatech.ma
- bakertilly.ma
- interact.ma
- inwi.ma
- adm.co.ma
- agentis.ma
- megaflex.ma
- popay.ma
- ahg.ma
- gcl.ma
- marine-maroc.co.ma
- pac-ocean.ma
- rcar.ma
- portnet.ma
- candy.ma
- bmcebank.co.ma
- iam.ma
- cimat.ma
- ba.co.ma
- seplan.ma
- poste.ma
- config.ma
- bkam.ma
- omnidata.co.ma
- cct.ma
- ca-cdm.ma
- cdm.ma
- amendis.ma
- tgr.gov.ma
- oulmes.ma
- ged.co.ma
- fr.ma
- it.ma
- tangermed.ma
- cat.co.ma
- cpm.co.ma
The full list can be downloaded from below.
This article is only a preliminary analysis and does not confirm a breach yet, a final confirmation will be provided as soon the breach is 100% confirmed, this article then will be updated.
Read more on CloudSEK's blog :

